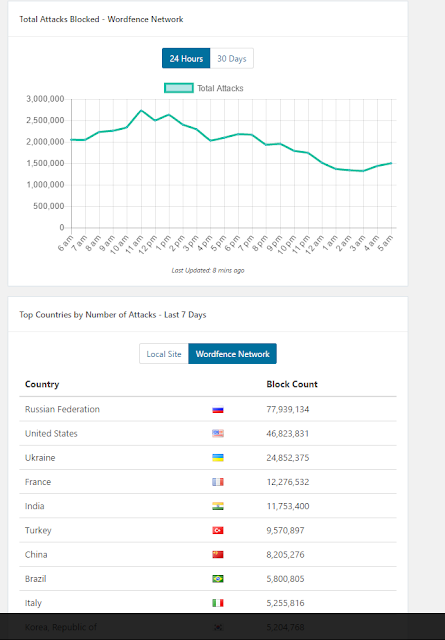
Welcome to my blog. My name is Adam Walker and I am excited to try what the kids call these days "blogging". Personally, I have never been a fan of owning a diary, or any sort of writing in general -- I am a complete math and science geek -- but this looks to be a riveting experience. Now, let me tell you a little bit more about myself. I am a senior at BASIS Scottsdale looking to document my experience during my research over my last trimester. I enjoy listening to any type of music, but my favorite would probably be grunge/rock/alternative. Speaking of music, I love to play guitar, and have been playing since 8 years ago. I have never not enjoyed guitar to give you an idea of how much I love it. Moving away from the arts now, I enjoy mechanical work on my car, a 2012 black Mustang (a car I am most proud of) and scrimmaging with friends in soccer.
Phew! I hope this all makes sense. It just seems to go in one ear and out the other when I try to explain it to people. In about a week and a half from the day this was posted, it will be my first day actually working on this project. Exciting times! Feel free to comment on any future posts regarding my projects or this one, if you are feeling up to it. I hope you have a wonderful day. This is Adam signing off.